5.1.1. Validate Controller¶
- class linotp.controllers.validate.ValidateController(*args, **kw)[source]¶
The linotp.controllers are the implementation of the web-API to talk to the LinOTP server. The ValidateController is used to validate the username with its given OTP value. An Authentication module like pam_linotp2 or rlm_linotp2 uses this ValidateController. The functions of the ValidateController are invoked like this
https://server/validate/<functionname>The functions are described below in more detail.
- check()[source]¶
This function is used to validate the username and the otp value/password.
- method:
- validate/check
arguments:
- user: The username or loginname
- pass: The password that consist of a possible fixed password component and the OTP value
- realm (optional): An optional realm to match the user to a useridresolver
- challenge (optional): optional challenge + otp verification for challenge response token. This indicates, that tis request is a challenge request.
- data (optional): optional challenge + otp verification for challenge response token. This indicates, that tis request is a challenge request.
- state (optional): The optional id to respond to a previous challenge.
- transactionid (optional): The optional id to respond to a previous challenge.
- returns:
JSON response:
{ "version": "LinOTP 2.4", "jsonrpc": "2.0", "result": { "status": true, "value": false }, "id": 0 }
If status is true the request was handled successfully.
If value is true the user was authenticated successfully.
- simplecheck()[source]¶
This function is used to validate the username and the otp value/password.
- method:
- validate/simplecheck
- arguments:
user: username / loginname
- pass: the password that consists of a possible fixes password component
and the OTP value
realm: additional realm to match the user to a useridresolver
- returns:
Simple ascii response:
- :-)
- in case of success
- :-(
- in case of failed authentication
- :-/
- in case of any error
- check_s()[source]¶
This function is used to validate the serial and the otp value/password.
- method:
- validate/check_s
- arguments:
serial: the serial number of the token
- pass: the password that consists of a possible fixes password component
and the OTP value
- returns:
- JSON response
- check_yubikey()[source]¶
This function is used to validate the output of a yubikey
- method:
- validate/check_yubikey
Parameters: pass (string) – The password that consist of the static yubikey prefix and the otp Returns: JSON Object - returns:
JSON response:
{ "version": "LinOTP 2.4", "jsonrpc": "2.0", "result": { "status": true, "value": false }, "detail" : { "username": username, "realm": realm }, "id": 0 }
- smspin()[source]¶
This function is used in conjunction with an SMS token: the user authenticates with user and pin (pass) and will receive on his mobile an OTP as message
- method:
- validate/smspin
- arguments:
- user: username / loginname
- pass: the password that consists of a possible fixed password
- realm: additional realm to match the user to a useridresolver
- returns:
- JSON response
- samlcheck()[source]¶
This function is used to validate the username and the otp value/password in a SAML environment. If linotp.allowSamlAttributes = True then the attributes of the authenticated users are also contained in the response.
- method:
- validate/samlcheck
- arguments:
- user: username / loginname
- pass: the password that consists of a possible fixes password component and the OTP value
- realm: optional realm to match the user to a useridresolver
- returns:
- JSON response
5.1.1.1. Authentication workflow¶
The following diagram denotes the authentication workflow. The loginname is reverse resolved to the userid by the useridresolver. Using the userid all tokens assigned to this user can be found in the token database.
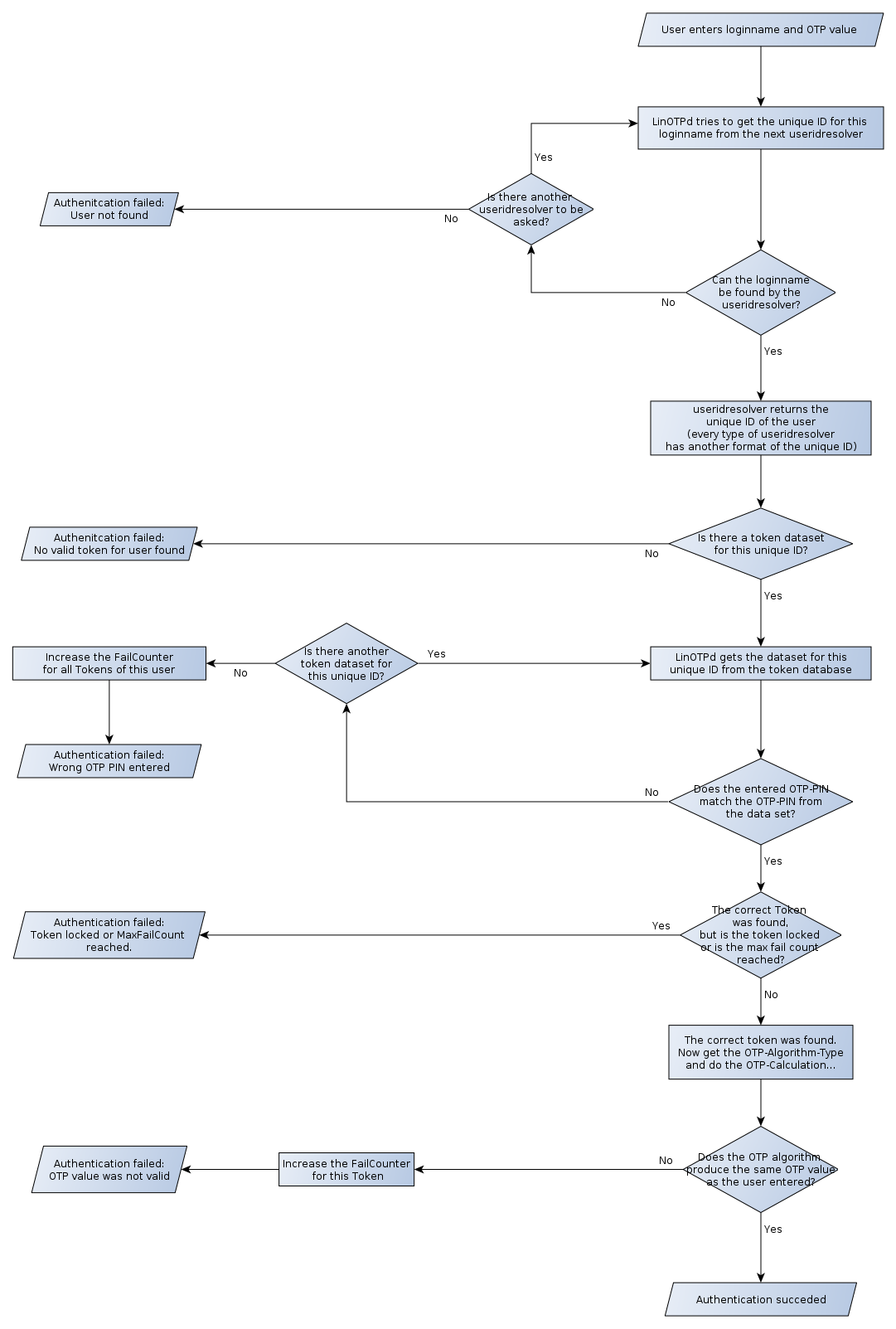
The authentication workflow in LinOTP
