3.1. UserIdResolvers and Realms - The Concepts¶
LinOTP implements a sophisticated concept of realizing multi-client capability.
LinOTP reads users from external user stores. These can be LDAP, Active Directory or Novell eDirectories or SQL servers or flat files like the UNIX /etc/passwd. These connections are configured using the UserIdResolvers.
LinOTP is also able to address any combination of as many of these UserIdResolvers as you need to.
Therefor each UserIdResolver has a unique name. Using the unique name of a UserIdResolver and the login name, a user can be biuniquely identified.
Imagine a user “Administrator” who might be located in every Active Directory LinOTP is accessing. By putting together the login name (Administrator) and the name of the UserIdResolver, all administrators can be distinguished easily.
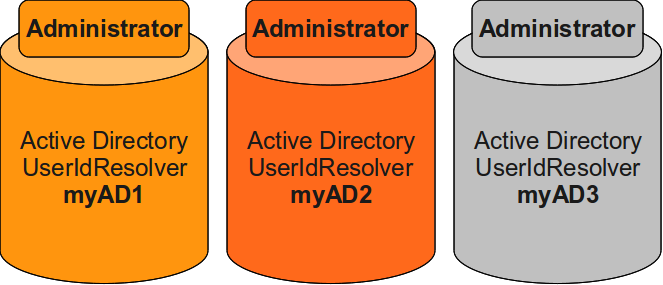
UserIdResolvers for different Active Directories¶
Another possible scenario for using several UserIdResolvers might be, that selecting all users from a directory would be to time consuming. Several UserIdResolvers could be configured to make only a portion of the users from a huge Active Directory available to LinOTP. Lets say, that all your users are located in one Active Directory but you only need to use a subset of your users. You can of course define intelligent search pattern to get the user subset. But you can also configure several LDAP UserIdResolvers to access different organizational units in your Active Directory:
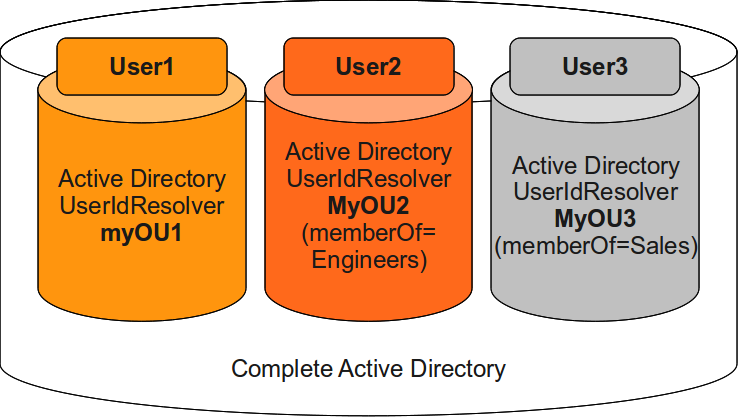
UserIdResolvers for different OUs in one Active Directory¶
User1 would be seen by LinOTP because the user is located in the OU, which is defined in UserIdResolver myOU1. User2 would be seen because the user is located in the OU, which is defined in UserIdResolver myOU2 and the user is in the group “Engineers”. User3 would be seen because the user is located in the OU, which is defined in UserIdResolver myOU3 and the user is member of the group “Sales”. To be able to provide the previous scenario to different Active Directories, it is also possible to group several UserIdResolvers to realms. When authenticating the UserIdResolver and the realm can be passed along with the username to be able to identify the user biuniquely.
3.1.1. Authenticating with Realms and UserIdResolvers¶
The LinOTP WebAPI, the PAM module and the FreeRADIUS module all can handle realms and UserIdResolvers. You may configure the realm and the UserIdResolver in the corresponding configuration files. This is described in the Installation guide: Installing Authentication Modules.
In the following example the the server FreeRADIUS 1 could be configured this way, that it always tries to authenticate the user1 only in the realm domain1. Users from other domains would not be able to authenticate to this RADIUS server. The server FreeRADIUS 2 does not have a special configuration. Users with the same username but from different domains can authenticate to this server. The user user1@domain1 will be found in the realm domain1 and the user user1@domain2 will be found in domain2. The server FreeRADIUS 3 will only authenticate users that can be found in the UserIdResolver “LDAP1”. All other users may not authenticate to this RADIUS Server.
This figure gives you an idea of the flexibility of using realms and resolvers:
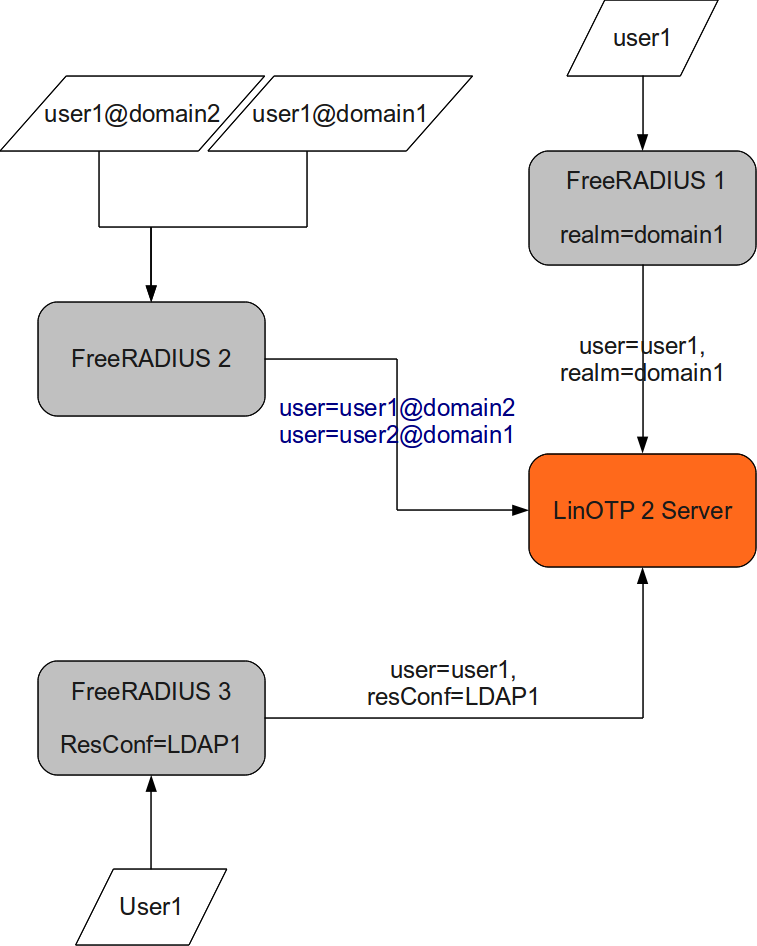
Several possible Configurations using realms and UserIdResolvers¶
