5.1. Tokentype Configuration¶
In here default values for certain types of tokens can be configured.
LinOTP Config part Token Config¶
5.1.1. Global - Default Settings¶
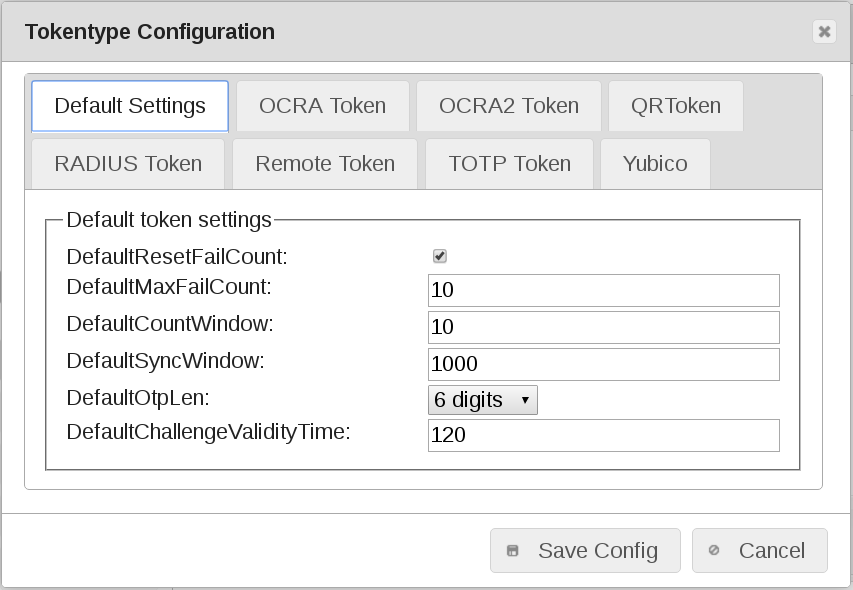
Token Config tab Default Settings¶
DefaultResetFailCount
If this is set to true (checked), a successful logon with a token will reset the counter of the failed attempts to zero.
This is a default value. You may change this per token.
DefaultMaxFailCount
The FailCounter is a counter per token, that counts the failed logon attempts. Here you can set, how often the user may attempt to logon with a token, before this token is locked.
This is a default value. You may change this per token.
DefaultCountWindow
This is the window where the LinOTP server searches a matching counter to validate the OTP value.
DefaultSyncWindow
For event based (HOTP) tokens this is the counter window, how many blank presses LinOTP will calculated further from its last known counter.
This is a default value. You may change this per token.
DefaultOtpLen
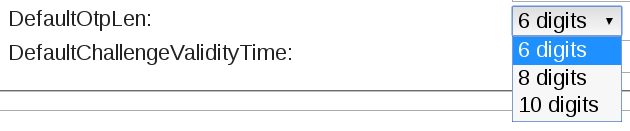
Tokens default OTP length¶
This is the length of the OTP value. This is used to split the OTP value from the OTP PIN. This is necessary for all token types.
This is a default value. You may change this per token.
DefaultChallengeValidityTime
This is the time in seconds for how long a created challenge can be used for authentication before it gets invalid.
5.1.2. OCRA Token - Default Settings¶
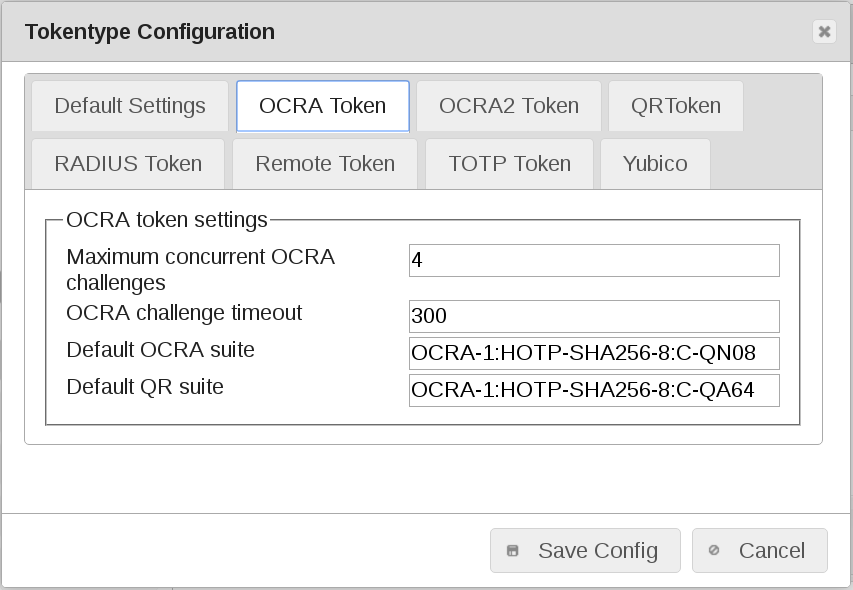
OCRA token default values¶
Maximum concurrent OCRA challenges
Maximum number of simultaneous OCRA challenges. Default ‘4’
OCRA challenge timeout
If the time after the challenge is rejected. This is a default (300) value. You may change this per token.
Default OCRA suite
An OCRASuite value is a text string that captures one mode of operation for OCRA, completely specifying the various options for that computation. An OCRASuite value is represented as follows:
<Algorithm>:<CryptoFunction>:<DataInput>
https://tools.ietf.org/html/rfc6287
Default ‘OCRA-1:HOTP-SHA256-8:C-QN08’
OCRA-1 Suite with: HOTP-SHA256-8: HTOP with SHA256 shortens to 8 digits: C: with counter - QN08: numerical Challenge up to 8 digits
Default QR suite
Default ‘OCRA-1:HOTP-SHA256-8:C-QA64’
OCRA-1 Suite with: HOTP-SHA256-8: HTOP with SHA256 shortens to 8 digits: C: with counter - QN08: numerical Challenge up to 64 digits
5.1.3. OCRA2 Token - Default Settings¶
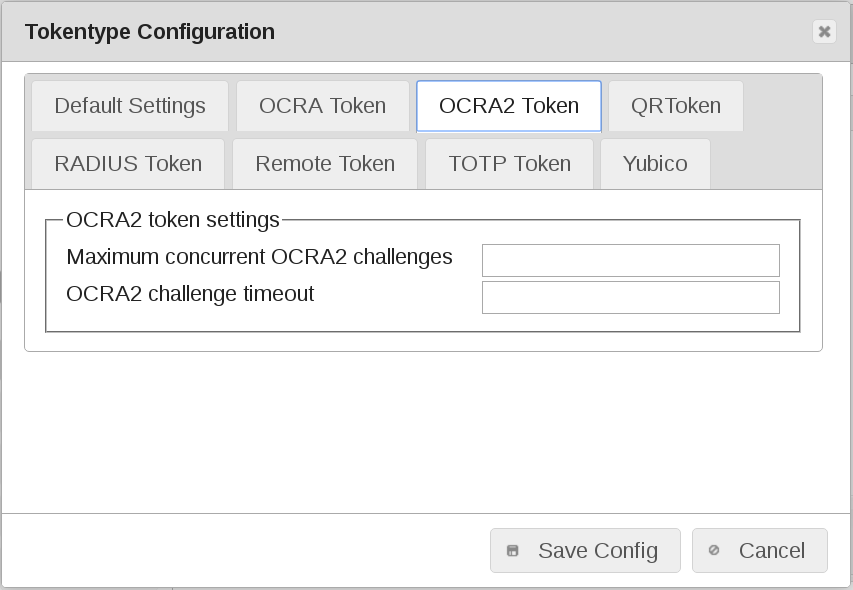
OCRA2 token default values¶
Maximum concurrent OCRA2 challenges
Maximum number of simultaneous challenges OCRA2
OCRA2 challenge timeout
If the time after the challenge is rejected. This is a default value. You may change this per token.
5.1.4. QRToken - Default Settings¶
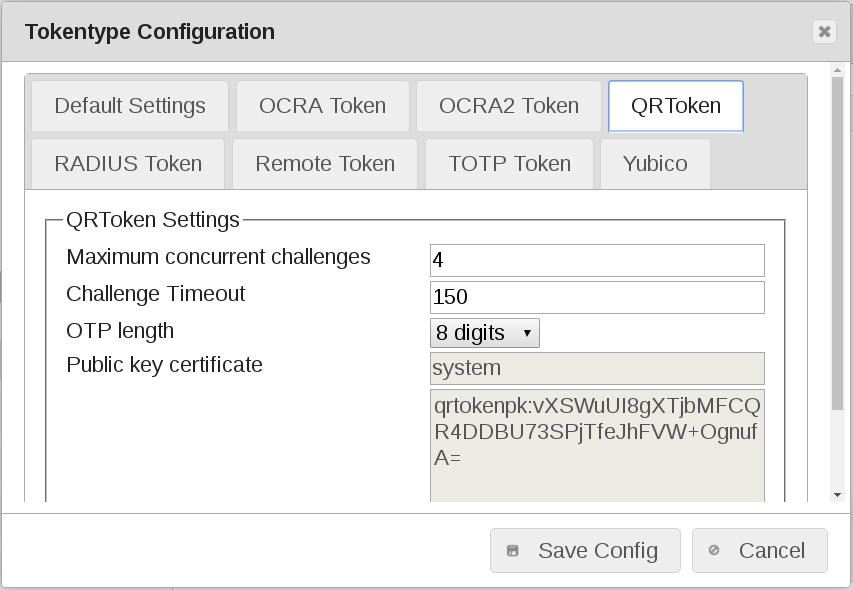
QRToken default values¶
Maximum concurrent challenges
Maximum number of simultaneous QRToken challenges. Default ‘4’
Challenge Timeout
The time (in sec) after the challenge is rejected. Default ‘150’
OTP length
This is the length of the OTP value. This is used to split the OTP value from the OTP PIN. This is necessary for all token types.
The default value is 8. You may change this per token.
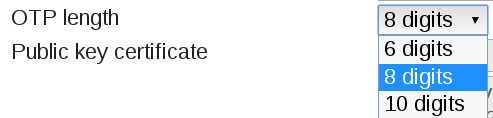
QRToken OTP length default values¶
Public key certificate
Defaults to ‘system’.
5.1.5. RADIUS Token - Default Settings¶
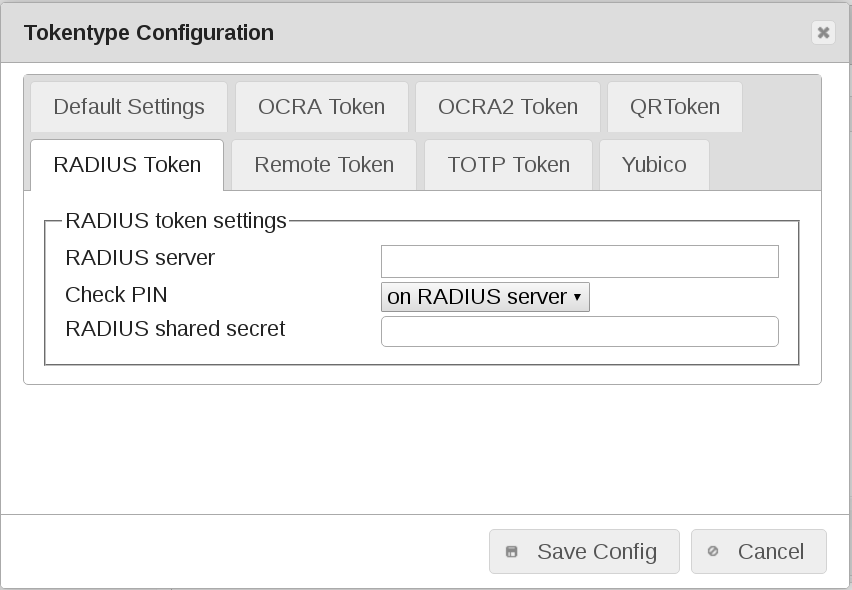
RADIUS token default values¶
RADIUS server
FQDN or IP address of the used RADIUS servers. Input a comma seperated list.
Check PIN
Check PIN ‘locally’ or remote ‘on RADIUS server’.
RADIUS shared secret
The secret is used to configure the local client on the RADIUS server.
5.1.6. Remote Token - Default Settings¶
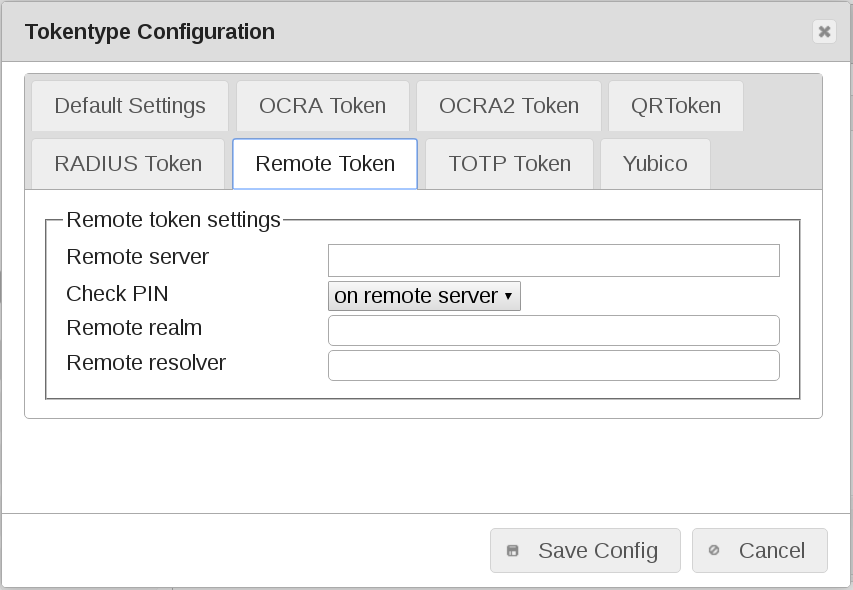
Remote token default values¶
Remote server
FQDN or IP address of the used LinOTP servers. Input a comma seperated list.
Check PIN
Check PIN ‘locally’ or ‘on remote server’.
Remote realm
User are identified in these realms on remote LinOTP. Input a comma seperated list, if empty ????
Remote resolver
User are identified in these resolvers on remote LinOTP. Input a comma seperated list, if empty ????
5.1.7. TOTP Token - Default Settings¶
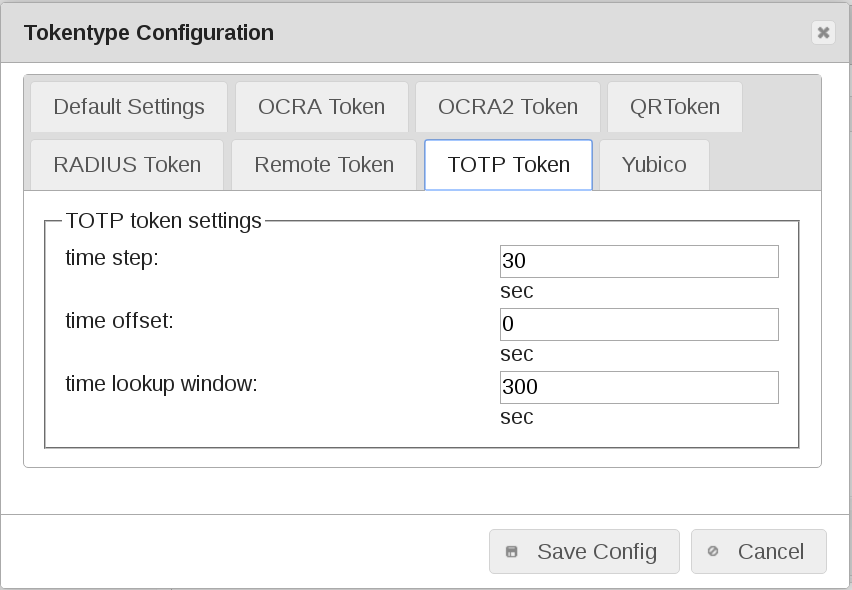
TOTP token default values¶
timestep
TOTP tokens are time based OATH tokens defined in RFC 6238. The counter is calculated from the UNIX system time. The counter increases either all 30 (default) or 60 seconds. So you need to enter 30 or 60 here.
This is a default value for enroll new token. You may change this per token.
time offset
This is the drift of the LinOTP clock from the TOTP token clocks. Usually you should have no default drift, but have your LinOTP server clock synchronized using NTP. So this should be set to 0.
This is a default value. You may change this per token.
time lookup window
LinOTP can calculate and compare the OTP values from some seconds before the current time and after the current time. A sensible value could be 60 or 120, so that LinOTP will calculate and compare OTP values 1 or 2 minutes before the current time and after the current time. LinOTP use as default 300 sec.
This is a default value. You may change this per token.
5.1.8. Yubico Token - Default Settings¶
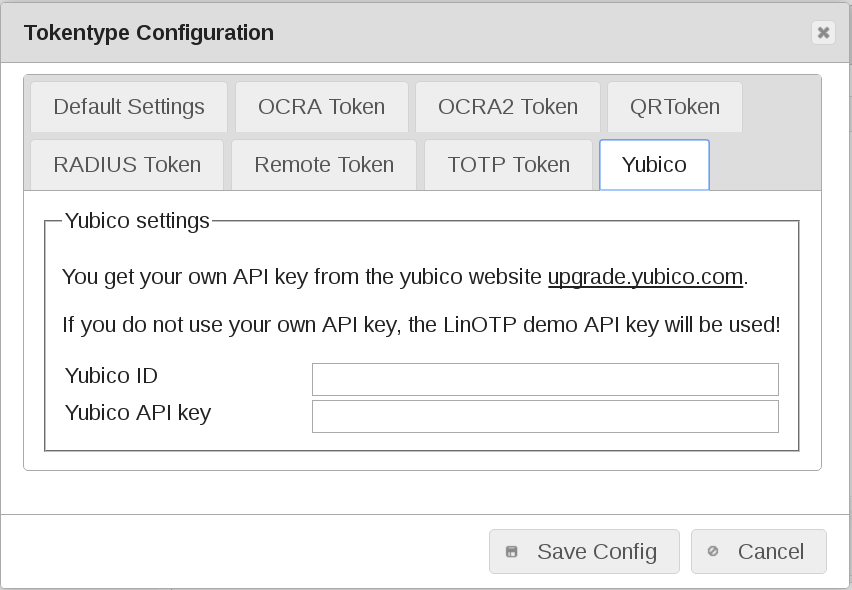
Yubico token default values¶
Yubico ID
Yubico includes a Public ID for each OTP, allowing YubiKeys to be associated with user accounts. This can be configured with the ‘YubiKey Personalization Tool’.
No default
Yubico API key
A shared symmetric key for use with the Yubico. It can be configured with the ‘YubiKey Personalization Tool’.
No default
