6.2.1. Provide CA certificates for HTTPS and LDAPS in the system store#
LDAP UserIdResolver Can be addressed with ldaps or StartTLS via SSL. For this LinOTP must check the validity and trustworthiness of the certificate. It is necessary that the LinOTP has the CA-Cert with complete chain available.
This can be done on two levels:
The complete chain is inserted in the Appliance configuration in the tab System -> Trusted Certificate Authoroties (copy and paste).
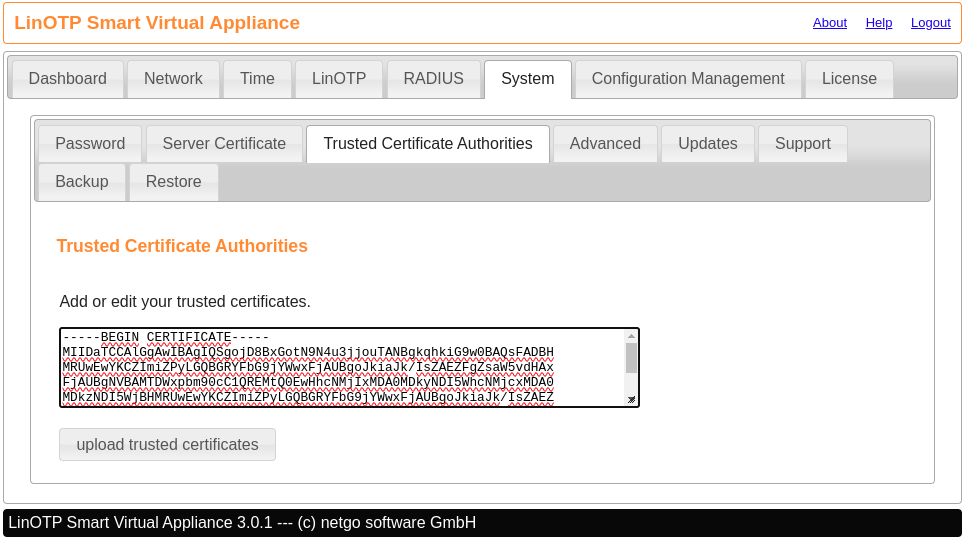
Alternatively and not simultaneously, the certificate can also be stored in the system store of the operating system.
Certificate chains for UserIdResolvers on OS level#
Providing the CA_Certificate#
the certificate exported from the Windows PKI must be converted to the PEM form. Details can be found at the end of the Howto.
store certificates in PEM format to /usr/local/share/ca-certificates/ - they should end on .crt
regenerate certificate store
update-ca-certificates
Converting PKCS#7 from the Windows PKI#
You have to install the certificate separately on all LinOTP’s it’s not covered by redundancy to have the full chain in the Windows-CA use the PKCS#7 format there you can check a box where you can include the full chain (coming from the sub-ca) commands to convert the PKCS#7 in linotp:
openssl pkcs7 -inform der -in ca-chain.p7b -out ca-chain.cer
openssl pkcs7 -print_certs -in ca-chain.cer -out ca-chain.crt
openssl x509 -text -noout -in ca-chain.crt
