1.5.8. Manage tokens#
You can now manage all your existing tokens. This includes the already described processes of enrolling and assigning tokens.
Unassign#
If a user does not need his token anymore, the token can be unassigned from the user.
The token will not be assigned to the user anymore and the OTP PIN of the token gets cleared.
Remove#
If a token is completely lost or is not needed anymore, the token can be removed from the token database.
Note
All entries about this token will remain in the audit trail.
Disable#
If a user should not use the token for authenticating – maybe because he forgot the token somewhere – the token can be disabled. This is reflected by the column “active”.
Note
Later you can enable the token again.
Reset fail counter#
The fail counter reflects how often the user failed to authenticate with this token.
The fail counter is increased under the following conditions. The last 6 or 8 characters are removed from the provided password. This is assumed to be the OTP value. The remaining leading characters are interpreted as the fixed OTP password/ OTP PIN. If LinOTP finds a token, which matches this OTP PIN but not the OTP values, the fail counter for this very token is increased. If LinOTP does not find a token, which matches the OTP password, the fail counters for all tokens assigned to this user are increased. If the fail counter reaches the the value of max fail counter, login with this token is not possible anymore and the fail counter will not be increased any further. If a user authenticated successfully the fail counter for this token is reset to zero.
Set Expiration#
In some scenarios tokens should be only usable for a certain amount time or authentication attempts. Starting with LinOTP 2.10 tokens usage can be limited regarding:
maximum authentication attempts
maximum successful authentications
time based (valid from and until)
The most convenient way to set the desired limits is to select the token in “Token View” and click on “Set Expiration” on the left side.
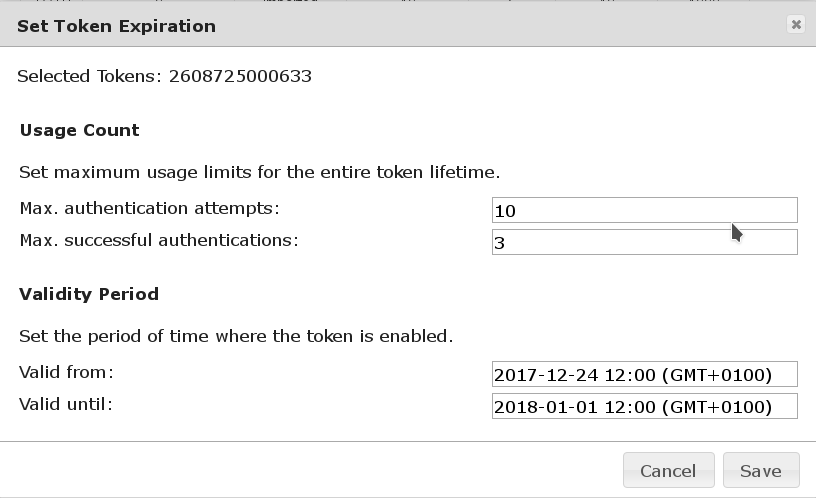
A configuration could look like this.
Note
Unwanted limits can just be left unconfigured (“unlimited”)
If one of the limits is exceeded the token can not be used anymore until the limits are changed again.
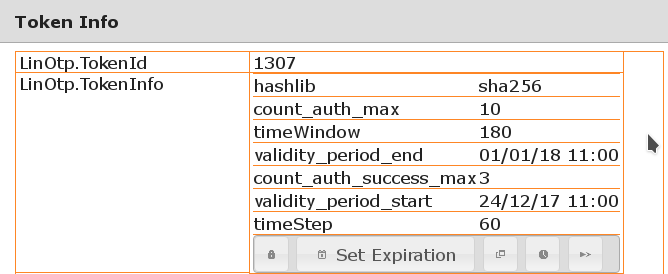
The expiration can be reviewed and reconfigured for a token later via the same interface or in the “Token Info”:
Resync token#
Event based tokens like the HOTP token work this way, that the token has a counter which is increased on every creation of every new OTP value. The LinOTP server also tracks this counter.
The LinOTP server has a “count window” defined per token. The server will try to validate the entered OTP value within this count window.
Logically the counter can run out of sync, when the new OTP values are not passed to the LinOTP server for authentication. When the user creates many new OTP values but only authenticates with the 20th OTP value while the count window on the server is only 10, then the server will not be able to find this OTP value within the count window and will fail to validate the OTP value.
The token is out of sync and needs to be resynced.
Note
You can also use the autosync function described in section System Config.
To resync the token manually
select a token
choose “Resync Token”
and enter two consecutive OTP values.
