Logins for administrative interfaces#
Overview#
Administrative interfaces are used for configuration and token management in LinOTP. While in the section Administrative Interfaces essentials are said about the API we want to be satisfied here on the GUI with the controller ‘linotp.controllers.manage’. This controller provides access to the web gui and its functionality. Other controllers for ‘Admin’, ‘System’, ‘Reporting’ and others work on the same basis regarding access conditions. The rights of the administrators are all controlled by policy.
LinOTP 3 is self-controlling in the authentication of administrators:
LinOTP 3 has its own user store for administrators
The user administration is divided into User, UserIdResolver (internal, LDAP, SQL) and Realm.
Each user is assigned rights via policy from the scope System and Admin
If no policy in the scopes System and Admin are effective, the users have full access (default after installation). The first policy must allow full access to at least one administrator, see here in the Policy section.
Administrative Users#
Administrative users are distinguished by their username and UserID. The username may be used in Policy under User to assign rights.
The first administrative user is created during the installation or after a restore. It is stored in an internal UserIdResolver of LinOTP.
These users can be managed via the GUI of the SVA https://<LinOTP_IPorFQDN>:8443 or via the command line tool ‘linotp’. These users are a suitable fallback if the predominantly active administrators are recruited from a group of Windows AD.
All administrative users are assigned to a UserIDResolver and belong to the realm ‘linotp_admins’.
UserIdResolver#
All resolvers that can be configured in LinOTP can be used as UserIdResolvers. It is to be avoided that users appear in different resolvers to determine the access rights clearly. The users maintained in the UserIdResolver can be uniquely distinguished by their UserID. All UserIdResolvers with administrative users are combined in the realm ‘linotp_admins’.
Realm#
The realm ‘linotp_admins’ is intended for administrative purposes and therefore marked accordingly (admin).
Policy#
By policy the administrators get rights in scope admin, system, audit, reporting_access and so on. As long as no policy is active in the System or Admin areas, all administrators have full access. As soon as the first policy becomes effective, it restricts the rights to the named users and UserIdResolver: Users in policies.
Manage the Administrators#
Create local Administrators from GUI#
In LinOTP 3 the administrator users are handled in a new way. The users are managed in a UserIDResolver now.
To manage the preconfigured Administration Users you can go to the SVA management interface (https://example.edu:8443) under the section LinOTP you can reset the password of the administrator you created on installation or add more administrators to the preconfigured resolver.
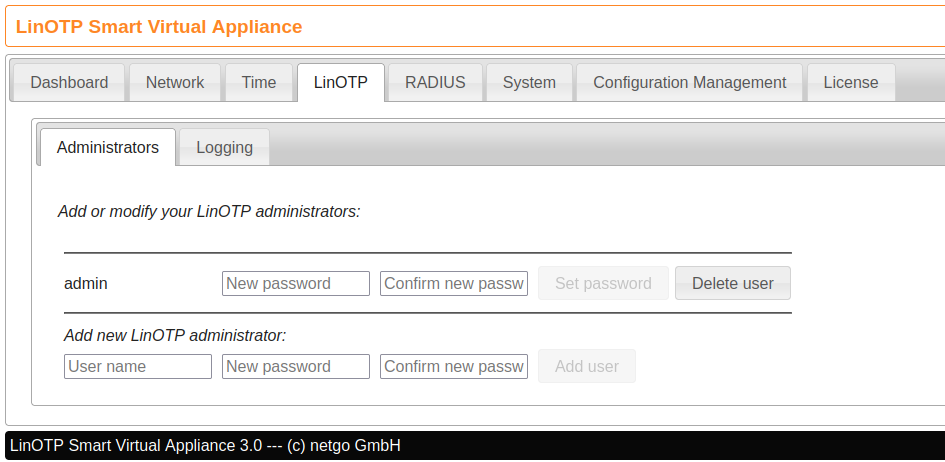
Managing LinOTP administrators#
Note
Only the Appliance administrators root and appadmin can change the passwords of the LinOTP token administrators.
Note
After adding, deleting or changing the LinOTP token administrators you need to activate the configuration as indicated.
The new login screen of LinOTP 3#
If you want to use a different resolver you can add a resolver of your choice under “LinOTP configuration” > “UserIdResolver”.
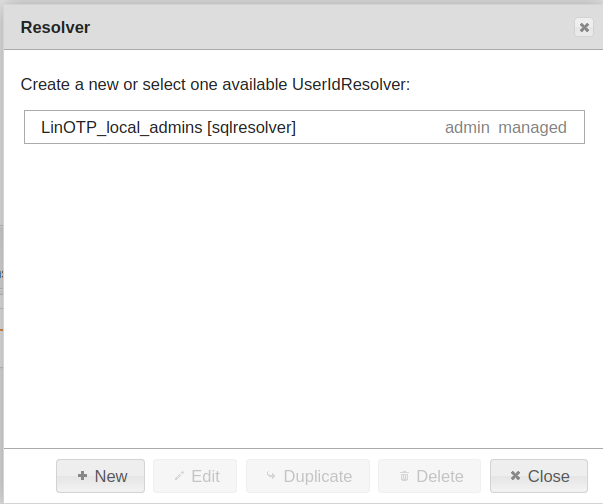
Managing UserIDResolvers#
You can add a new UserIdResolver.
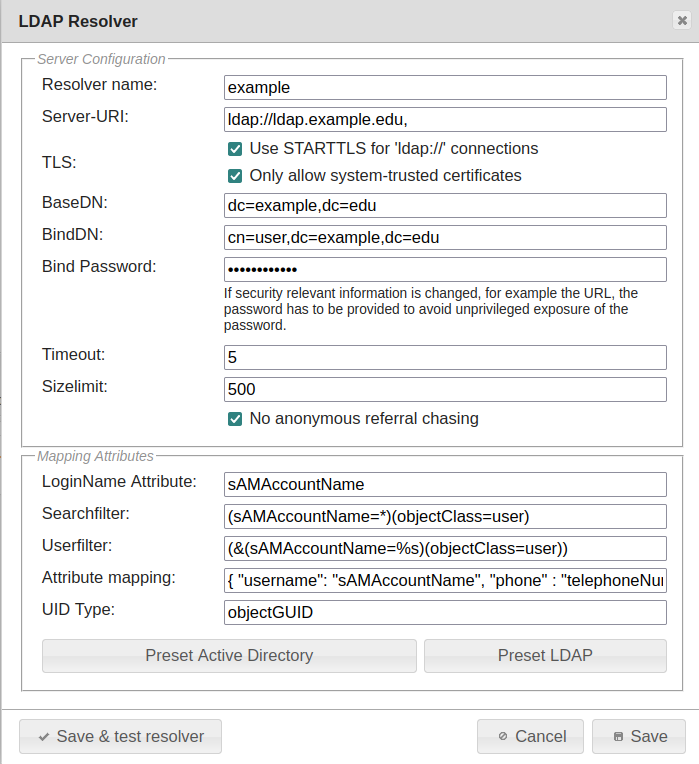
This is an example for a LDAP UserIDResolver#
This resolver can be added to the linotp_admins realm under “LinOTP configuration” > “Realms”
The linotp_admins realm#
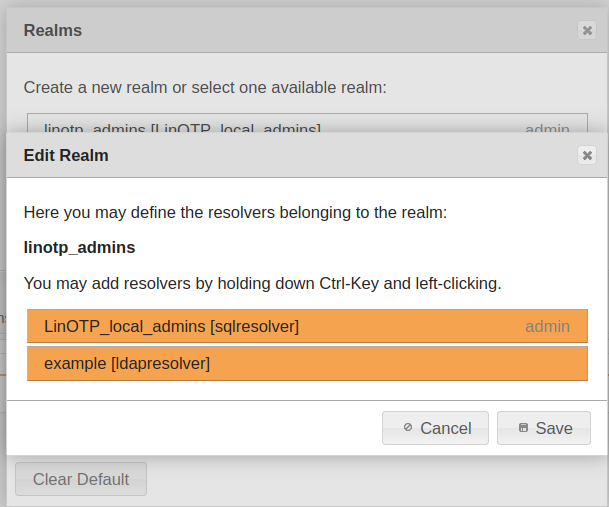
To add multiple UserIDResolvers to the realm click on them with the control button pressed#
Note
Per default (without admin policies) every user in the linotp_admins realms has full rights to the management interface of LinOTP.
Create local Administrators from Shell#
With LinOTP 3 the command line tool linotp is provided. This can be used to manage the local admin users. It is available after logging in via the SSH protocol.
The appropriate description can be found here: Tools.
To maintain administrative users use:
linotp local-admins list
linotp local-admins add <localadminname>
linotp local-admins password --password <localadminname>
