3.2. Checklist#
Before installing LinOTP you should think about the following questions. This will make it easier for you to understand and plan your setup.
3.2.1. Decide which distribution you want to use#
The LinOTP server is supplied as a virtual application based on Debian 12. It installs the operating system and all necessary components and carries out the basic configuration. LinOTP is also available as a ready-to-use hardware appliance.
LinOTP servers can also run on other Linux distributions, but then the installation process requires some additional steps. Decide whether it is necessary for you to choose the installation on a different distribution or whether you want to use the virtual appliance.
3.2.2. Decide which token database you want to use#
Decide if you want to use the internal token database [1] on the LinOTP server (installed with the virtual appliance) or if you need to use an external database. You might have a dedicated database department that takes care of redundancy, availability and backups. The encryption key for the database stays on the LinOTP server, so that in case of using an external database no sensitive data will be exposed to another IT department. Have the database name and the username to access the external database at hand. For more information on the token database see Token database.
3.2.3. SSL certificate#
The communication to the LinOTP server is secured via SSL. During the installation a self signed certificate with SHA256 and 2048 bit RSA key will be generated.
You may also decide to replace this certificate with a certificate issued by a company CA.
3.2.4. LinOTP Admin#
Starting with LinOTP version 3.2, LinOTP no longer relies on web server based authentication. The admin authentication is done by LinOTP which uses a dedicated resolver and a dedicated admin realm which can be depolyed with the LinOTP command line tool:
$ linotp local-admins password admin
For more details about the usage of the LinOTP command line tool you can type
$ linotp local-admins --help
For a deeper technical background have a look at the chapter about admin authentication: Authentication.
3.2.5. User databases#
Determine where your users are located and get access to this database. If your users are located in an LDAP/Active Directory or in an SQL server, you will need to have a user with corresponding credentials to access this user database.
If your users are located in an LDAP or SQL server, you will also need to determine, which attribute or column holds the login name.
3.2.6. User tokens#
You need to decide, what tokens you are going to use. If you will use SafeNet eTokenNG OTP, you will need to install the SafeNet PKI Client and the native LinOTP management client - as these tokens need to be enrolled being plugged into the USB port.
3.2.7. Authentication#
Where and how will the authentication be done? If you are using RADIUS, you need to configure
your RADIUS clients accordingly. You might want to change the RADIUS shared secret by editing
the file /etc/freeradius/clients.conf on the LinOTP server. When you are using the appliance
you can use the web interface to configure the RADIUS clients and change the shared secrets.
3.2.8. Location in your network#
The following figure shows the ports that LinOTP uses to communicate. This should help you if you want to place your LinOTP server within a separated subnet or demilitarized zone.
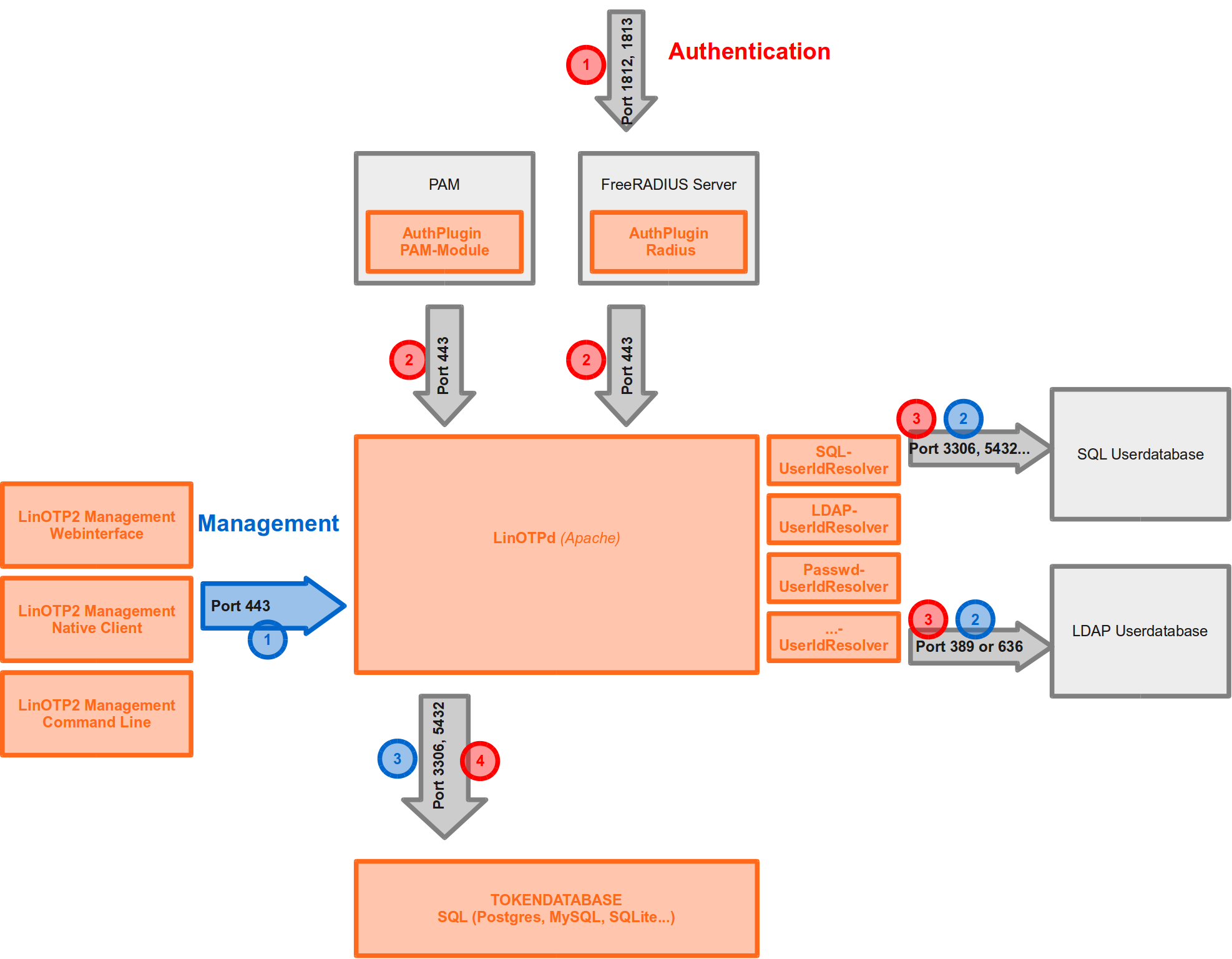
LinOTP workflow and network communication#
In figure LinOTP workflow and network communication blue numbers represent steps for managing LinOTP and red numbers represent steps when authenticating with LinOTP. For managing and for authenticating the management clients and the authentication modules communicate with the LinOTP core on port 443 (blue 1 and red 2).
You usually will do the authentication via RADIUS. The LinOTP RADIUS plugin communicates with the LinOTP core on port 443, while the application (e.g. Firewall, SSL VPN) you are logging in to communicates to the FreeRADIUS server which by default is also located on the LinOTP server via Port 1812 and 1813 (red 1).
The LinOTP core communicates to the user database and the token database.
The user database will be an existing database like an SQL server or an LDAP server. So the LinOTP server needs to contact this LDAP server or Active Directory via port 389 or 636 (LDAP or LDAPs). If the users are stored within an SQL server, the LinOTP server needs to be able to reach those ports.
You may use the internal token database with the LinOTP server or you might want to use an external SQL server as your token database. In the later the LinOTP server needs to reach this external SQL database.
